In a data breach that has caused anxiety about security and privacy, Dell, a technology hardware giant, has admitted to its occurrence having affected 49 million customer records. The unsecured API linked to a partner portal allowed hackers to swipe a huge amount of information about customers from Dell’s database.
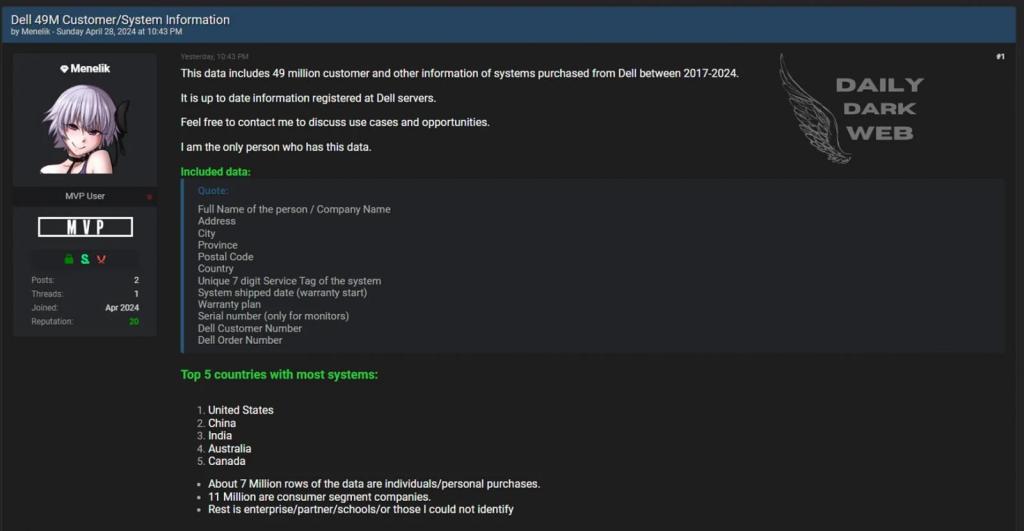
Source: Daily Dark Web
Methodology of the Breach
The hacker, known as Menelik, shared his methodology with TechCrunch .
“Believe me or not, I kept doing this for nearly 3 weeks and Dell did not notice anything. Nearly 50 Million requests…After I thought I got enough data, I sent multiple emails to Dell and notified the vulnerability. It took them nearly a week to patch it all up,” Menelik said.
Dell on the other hand, responded with “Let’s keep in mind, this threat actor is a criminal and we have notified law enforcement.”
- Exploiting Partner Accounts: The threat actor created multiple “partner” firms known by different names for multiple accounts thereby leading in access to sensitive customer records.
- Scraping Customer Data: They stole huge amounts of client data directly from Dell’s servers including personal particulars and purchase information.
- Persistence and Volume: For nearly three weeks, the perpetrator launched an unyielding onslaught of appeals that led to almost 50 million records.
- Reporting: They emailed Dell on April 12th and 14th to report the bug to Dell security team

Source: Menelik
“Prior to receiving the threat actor’s email, Dell was already aware of and investigating the incident, implementing our response procedures and taking containment steps. We have also engaged a third-party forensics firm to investigate.”
Stolen Data Details
The exposed data has customer order data, including warranty information, service tags, names, locations, customer numbers, and order numbers.
The hacker, Menelik says the stolen customer records include the following hardware breakdown:
- Monitors: 22,406,133
- Alienware Notebooks: 447,315
- Chromebooks: 198,713
- Inspiron Notebooks: 11,257,567
- Inspiron Desktops: 1,731,767
- Latitude Laptops: 4,130,510
- Optiplex: 5,177,626
- Poweredge: 783,575
- Precision Desktops: 798,018
- Precision Notebooks: 486,244
- Vostro Notebooks: 148,087
- Vostro Desktops: 37,427
- Xps Notebooks: 1,045,302
- XPS/Alienware desktops: 399,695
Mitigation Efforts
Incident response protocols were deployed by Dell, containment strategies were employed, and external forensic experts were contracted to investigate and fix vulnerabilities.
Conclusion
Dell has advised customers to remain vigilant at all times by reporting any suspicious activities associated with their accounts or purchases as soon as possible.
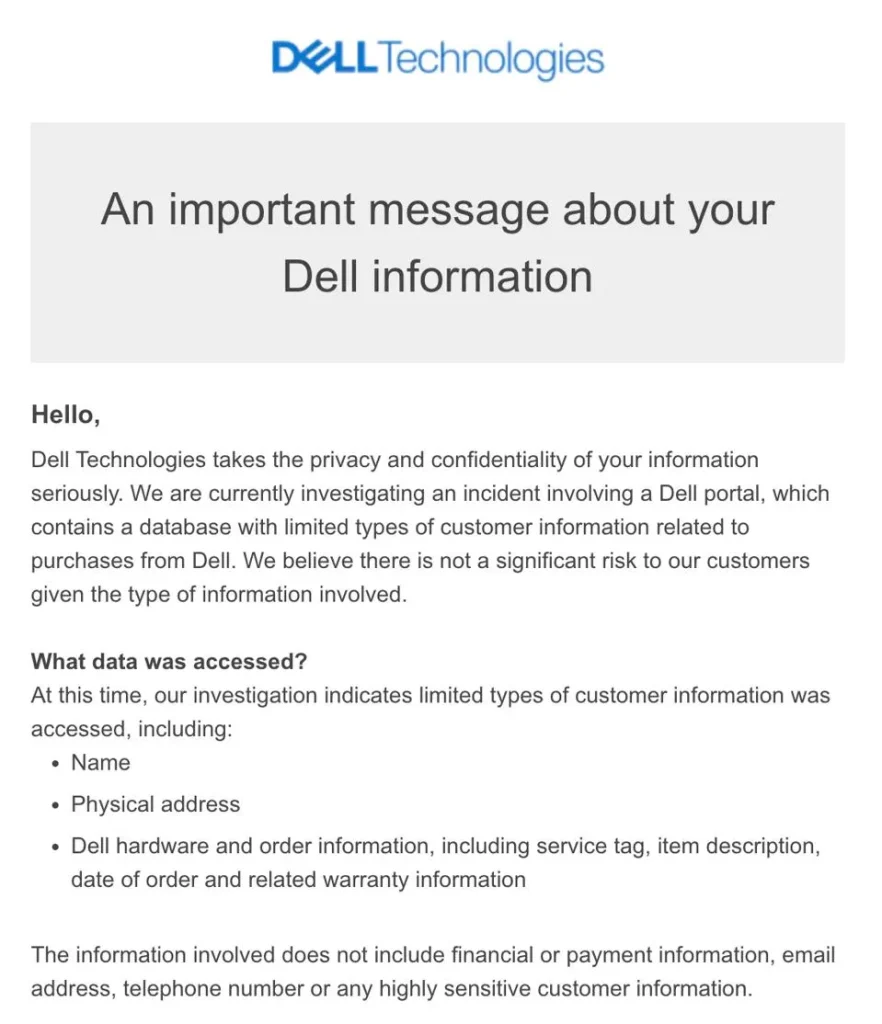
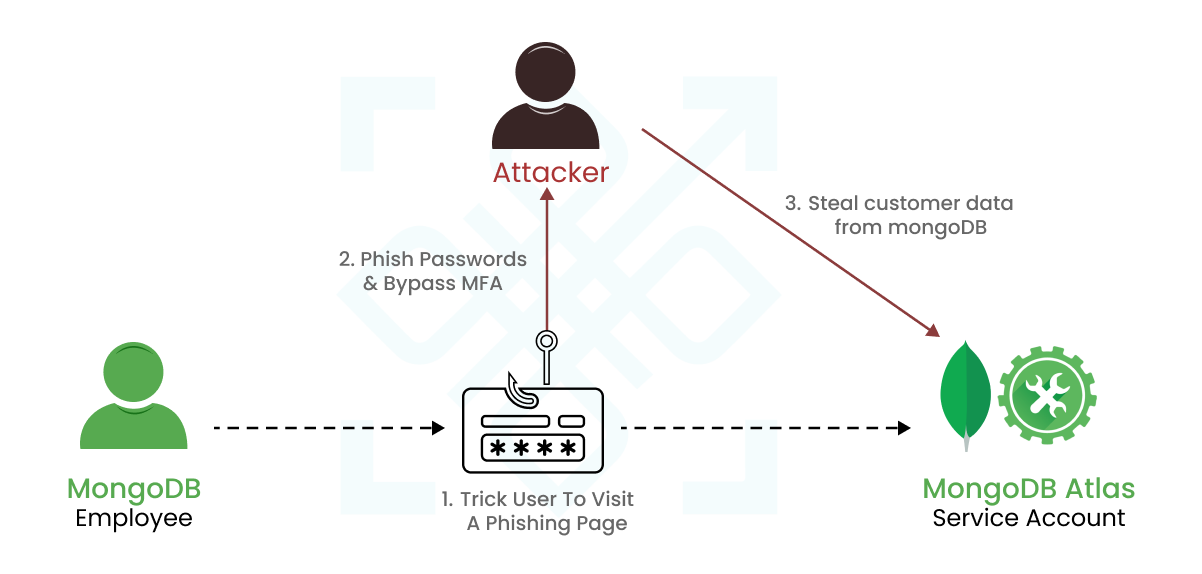
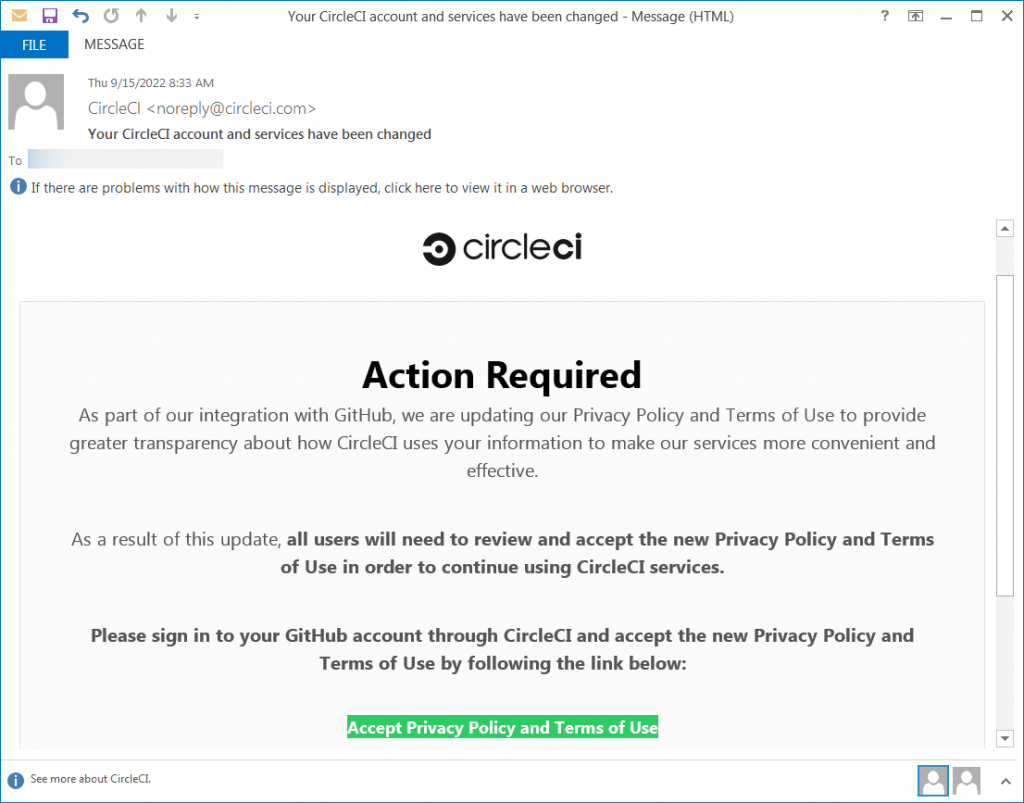
The 49 million customer purchase data between 2017-2024 looks like the perfect phishing bait. Anyone posing as dell representative can trick users into clicking links and being set up for credential theft.
We need to prevent a phishing incident like those that rocked Okta, Dropbox and Lastpass. It becomes imperative to fortify your organization with robust authentication methods. Embracing passwordless authentication could be precisely the solution needed. After all, if you don’t possess traditional credentials, they can’t be stolen, can they?
Read Also
Massive Data Breach: 125 Million Records Exposed Due to Firebase Misconfiguration