Breach Chronicles: MongoDB’s Unsettling Security Saga Unfolds
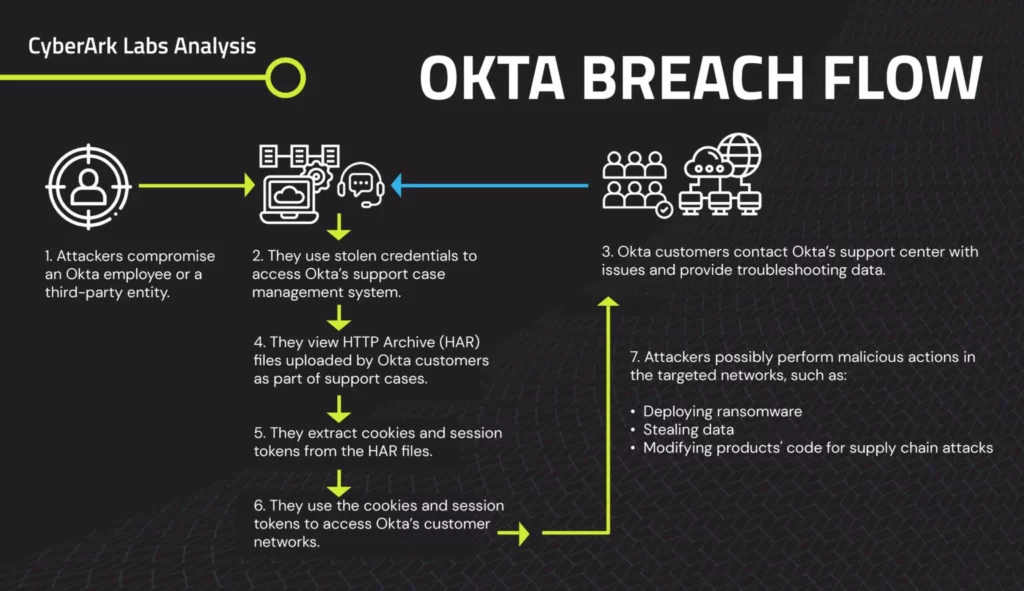
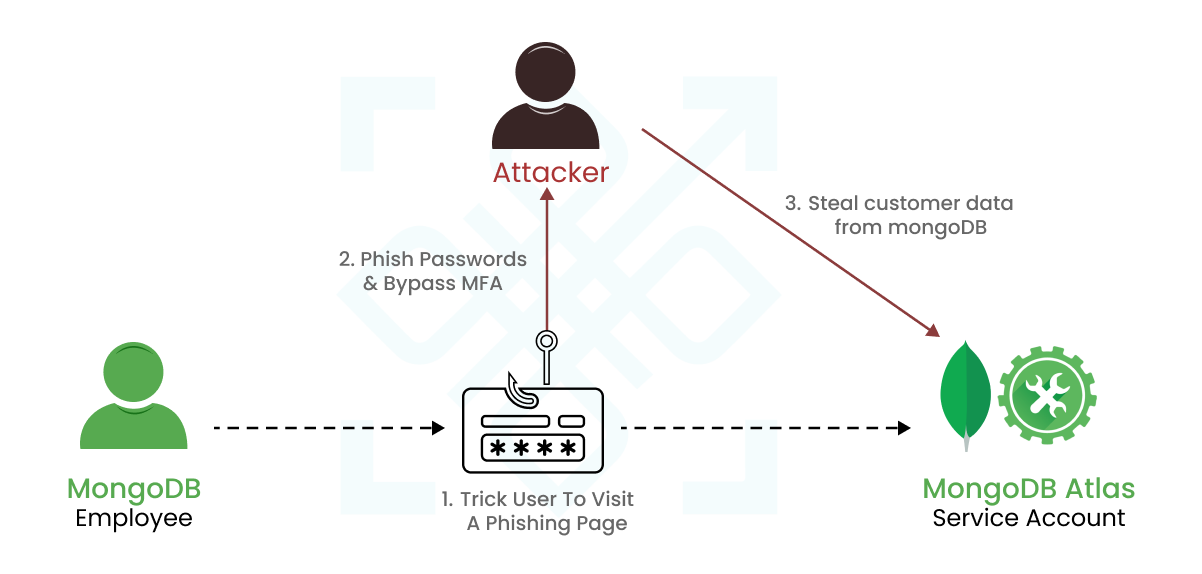
On December 13, 2023, MongoDB, a prominent US-based open-source NoSQL database management system provider, faced a substantial security incident. This breach of MongoDB Atlas, a fully-managed cloud database, unfolded as unauthorised access infiltrated corporate systems, laying bare customer account metadata and contact information. The assailants employed a cunning phishing attack, exploiting support service applications. The consequences were dire – a trove of sensitive data, including customer names, phone numbers, and account details, left exposed in the turbulent aftermath of this cyber storm.
Intrusion Footprints: A List of IPs Disclosed
In a proactive move, MongoDB disclosed a comprehensive list of external IP addresses on their alerts page. These IPs were strategically employed by the unauthorised third party. Organisations are strongly advised to meticulously scrutinise their networks, diligently searching for any ominous signs of suspicious activity intricately linked to these disclosed IPs. If you spot these IPs, you’ve got unwelcome guests. Remember it’s time to act, and act fast.

Phishing & Social Engineering – The Achilles’ Heel of Multi-Factor Authentication
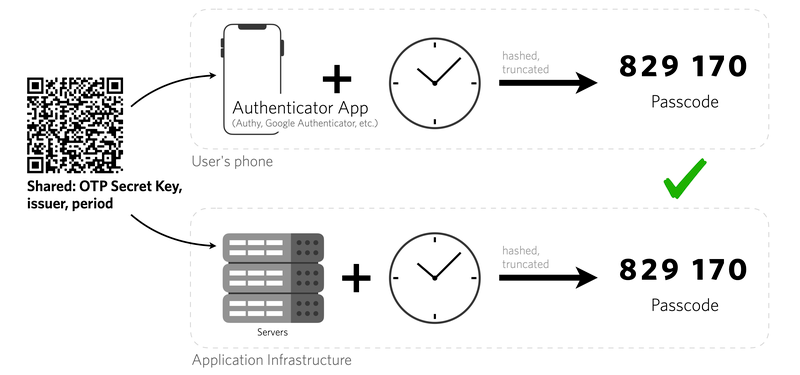
MongoDB issues a resolute counsel to its user base, emphasising the critical need to bolster defences against the looming threats of social engineering and phishing. In response, the company advocates the implementation of multi-factor authentication (MFA), urging users to promptly update their MongoDB Atlas passwords as an additional layer of security.
Phishing attacks or social engineering can bypass and disable all types of MFA solutions, as seen time and again. The security incident under discussion started with phishing attacks. So implementing MFA will have zero security advantage but will only increase the cost, efforts and complexity of authentication.
GoPasswordless – The best protection for MongoDB
Going passwordless with PureAUTH will benefit in 2 broad ways to protect MongoDB or any other enterprise applications –
- Secure Authentication – PureAUTH offers passwordless authentication which is secure from phishing & social engineering attacks.
- Resilience in case of data breach – If data from the database like MongoDB is leaked due to mis-configurations, 0-day vulnerability or insider attacks etc, the adversary will not find any passwords, MFA seeds, swap-able public keys, or any usable data to carry out unauthorised access elsewhere.
Conclusion
Amidst the gloom, MongoDB presents a silver lining: Passwordless Authentication. It’s a call to transcend traditional password reliance for a more secure future. Fortify your defences with passwordless security. MongoDB users, the future beckons. Embrace the resilience of passwordless authentication, reinforce your security posture with PureID, and navigate the cyber security landscape with renewed strength. Passwords? Pfft, that’s so yesterday. The journey continues—Passwordless Authentication awaits.