Connect with Us!
Subscribe to receive new blog post from PureID in your mail box

In 2023, developers inadvertently leaked a staggering 12.8 million secrets on public GitHub repositories, marking a concerning 28% increase from the previous year. This revelation underscores the security challenge faced by GitHub, as highlighted in a recent report by GitGuardian, a leading security vendor in the software development realm.
Despite the alarming number of leaked secrets, GitGuardian found that a staggering 90% of these exposed secrets remained active even five days after the initial leakage. Shockingly, only a mere 2.6% were revoked within one hour of receiving notification via email.
The report adds to the ongoing security challenges faced by GitHub. Since mid-2023, attackers have exploited GitHub's ecosystem, employing sophisticated tactics to infiltrate legitimate repositories and spread malware. These incidents serve as a reminder of the ongoing challenges in securing the software supply chain.
The most commonly leaked secrets included Google API keys, MongoDB credentials, OpenWeatherMap tokens, Telegram Bot tokens, Google Cloud keys, and AWS IAM. These leaked credentials could potentially grant unauthorised access to sensitive enterprise resources, posing a significant threat to organisational security.
GitGuardian's report also shed light on the growing popularity of AI services, with a notable increase in leaks of OpenAI API keys and HuggingFace user access tokens. These findings underscore the need for heightened security measures in the rapidly evolving landscape of artificial intelligence.
The IT sector emerged as the worst offender, accounting for 65.9% of the total leaked secrets, followed by education, science & technology, retail, manufacturing, and finance and insurance.
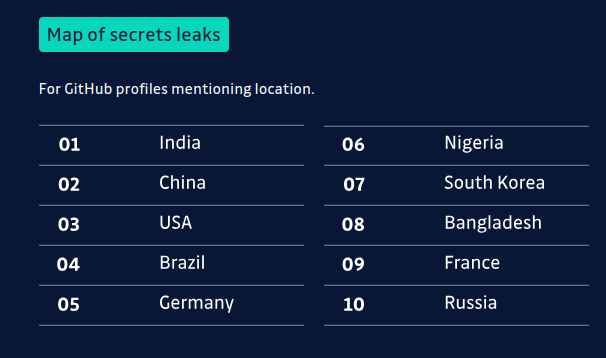
It's concerning to see India leading the charge in secret leaks, underscoring the necessity of bolstering security practices in CI/CD pipelines. This serves as a reminder of the critical need for enhanced vigilance in safeguarding sensitive data.
GitGuardian urged organisations to not only detect but also remediate these leaks effectively. While detection is crucial, remediation efforts are equally essential in mitigating the risks associated with leaked secrets. Additionally, organisations can enhance their security posture by leveraging advanced authentication frameworks such as PureAUTH's CASPR module.
This module ensures codebase integrity with cryptographic verification. By implementing robust security measures and utilising advanced authentication solutions, organisations can better safeguard their data.
In conclusion, the findings from GitGuardian's report underscore the pressing need for organisations to prioritise security measures to safeguard sensitive data and prevent unauthorised access to critical resources. The threat posed by millions of malicious repository forks since mid-2023 further highlights the importance of bolstering GitHub's security infrastructure. By adopting advanced authentication frameworks such as CASPR, organisations can bolster their defences against security threats and ensure the integrity of their codebase.
PureID helps enter prises to remove secrets like passwords, static keys, access tokens with its passwordless technology. By adopting it's other advanced authentication frameworks such as ZITA - Just-In-Time-Access & CASPR code-commit protection, organisations can bolster their defences against security threats and ensure the integrity of their codebase.
Subscribe to receive new blog post from PureID in your mail box