Connect with Us!
Subscribe to receive new blog post from PureID in your mail box

PureID’s passwordless authentication platform PureAUTH, is a cloud based Single Sign On (SSO) solution. PureAUTH uses certificates (digital signatures) provided by an organisation, to uniquely identify its users, in a secure way.
PureAUTH can be used as a secure, cryptography or certificate based alternative to Passwords and Two Factor (2FA) or Multi Factor Authentication (MFA) solutions, as prescribed by various standards.
In this article we discuss
Traditionally, applications authenticate users using passwords. For additional security along with passwords, 2FA or MFA are also sent to application on the same channel. This authentication method is found to be vulnerable to phishing and other man in the middle attacks. An adversary can trick users to share passwords and 2FA/MFA token, on a phishing page and use it to impersonate user, and gain unauthorised access to the application.
PureAUTH provides a secure alternative to passwords and 2FA /MFA based authentication. Organisation's user is provided with an AuthVR5 authenticator app which holds cryptographic keys, certificates (digital signatures), seeds (for generating Pseudo Random token), which are unique for every user.
AuthVR5 sends out of the channel authentication request, directly to the PureAUTH server which consists of user's certificate and one time token which is bound to the user's session with the application.
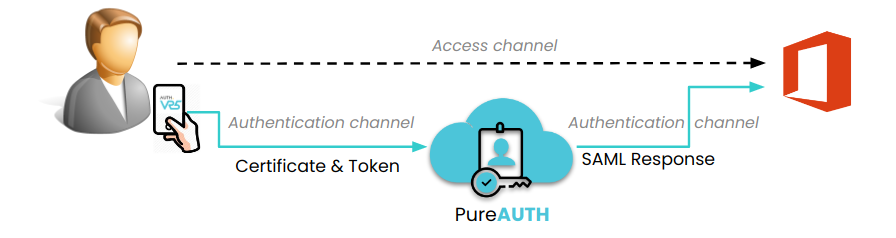
Since the authentication request is sent out of the channel, the data in the request cannot be obtained by phishing, neither it can be used for any other session apart from the one it was generated for.
The authorisation & session management remains unaffected by introduction of PureAUTH. The user authentication security is enhanced by PureAUTH with the use of certificates (digital signatures), extensive logging, and risk assessment of user's device, from which the application is being accessed.
PureAUTH provides the required controls and complies with recommendations of various Industry and Regulatory standards, for user authentication and access control. Few widely used standards that PureAUTH complies with are as follows -
ISO/IEC 27001 is the world’s best-known and widely exercised standard for Information Security Management Systems (ISMS). The annexure A, section 9 of ISO/IEC 27001, is all about access control procedures. The aim of Annex A.9 is to safeguard access to information and ensure that employees can only view information that’s relevant to their work.
From Annexure A.9, we are focusing on section A 9.4.2, according to which
Access to systems and applications must be controlled by a secure log-on procedure to prove the identity of the user. This can go beyond the typical password approach into multi-factor authentication, biometrics, smart cards, and other means of encryption based on the risk being considered.
Secure log on should be designed so it cannot be easily circumvented and that any authentication information is transmitted and stored encrypted to prevent interception and misuse.
In this section we answer a few relevant questions that are part of ISO 27001 Standard's questionnaire form, that can help our customers applying for similar standards.
| ISO 27001/2 STANDARDS | Why it is needed | How PureAUTH helps |
| Do you adopt multi factor authentication (MFA) for secure user access? | Makes access controls more robust and enhances their effectiveness to verify a user's identity. | Yes, PureAUTH is an authentication solution that uses multiple factors like cryptographic signatures & device fingerprints to securely identify user |
| Do you give all users unique login credentials? | Ensures that nobody can log on to the system without uniquely identifiable credentials. | Yes, the certificate or digital signatures are unique for every user and device fingerprint is unique for every device |
| Do you enforce the secure use of passwords and verify a person is the one claimed? | Strengthens unique network login credentials with context-aware access restrictions and user reminders which help verify that a person seeking access to the network and the information within is genuinely who they say they are. | Not Applicable for PureAUTH, as it is a passwordless authentication solution that uses cryptographic keys, certificates (digital signatures) to identify user |
| Do you restrict users from sharing logins? | Prevents concurrent logins with the same set of user credentials — helping to eradicate dangerous password sharing practices. | Yes, PureAUTH uses digital signatures embedded & paired to user's personal device secured by further layer of device based authentication. This makes sharing of signatures with other user and using it from another device impossible. |
| Do you restrict network access on a job-role basis? | Enables the administrator to set granular access rights to different types of employees to ensure that they can only access the information they need to do their job. | Yes, PureAUTH supports policy based regulation of user access that considers user's role, device risk and sensitivity of the application being accessed |
| Do you review network access for employees who change roles in the organisation? | Enables administrators to easily change access rights (permanently or temporarily) for individual users groups of users or organisational units. | Not Applicable, Authorisation is managed outside of the scope of PureAUTH |
| Do workstations automatically log users off the network following a period of inactivity? | Automatically logs off a session after a specific length of idle time to prevent unauthorised users accessing information from unattended workstations. What’s more UserLock can set authorised time frames for certain users’ access and force workstations to log off outside these hours. | Yes, PureAUTH supports Single Log Out (SLO) and respects the session timeouts enforced by respective applications |
PureAUTH passwordless authentication solution is not only compliant with all leading (and upcoming) industry and regulatory standards, but is also the most secure authentication and access management platform. Some of its advantages over traditional Passwords & Multi Factor Authentication solutions are as follows
| Risks | PureAUTH | Passwords + MFA |
| Phishing | Unaffected by Phishing | Vulnerable to Phishing attacks |
| Social Engineering | Unaffected by social engineering or insider attacks | Vulnerable to Social Engineering |
| Account Sharing | Not possible, compliant | Account sharing is possible |
| Admin/Tech Support | Completely self serviceable. No admin assistance or tech-support needed | Dependency on Admin, tech support for resetting of passwords and MFA device |
Just like Passwords and Two-factor or Multi Factor authentication systems, PureAUTH Passwordless authentication solution can be used to ensure secure access to the most sensitive information systems, applications, and programs like Engineering & Dev-Ops resources, security systems, VPNs, PAM solutions, SaaS services, cloud consoles, communication suites, CRM solutions etc.
For further information on compliance & certification, you can visit https://trust.pureid.io
Subscribe to receive new blog post from PureID in your mail box